

What is digital identity?
Your digital identity is the fingerprint you leave across the internet, a living map of who you are.
Your digital identity is more than just your name or email; it stretches from your social media profiles and crypto wallet addresses to your device fingerprints and even the rhythms of your daily browsing habits. In the fast-moving world of cryptocurrency, where identity and financial access often overlap, digital identity theft isn’t just a nuisance; it’s an open door to your assets.
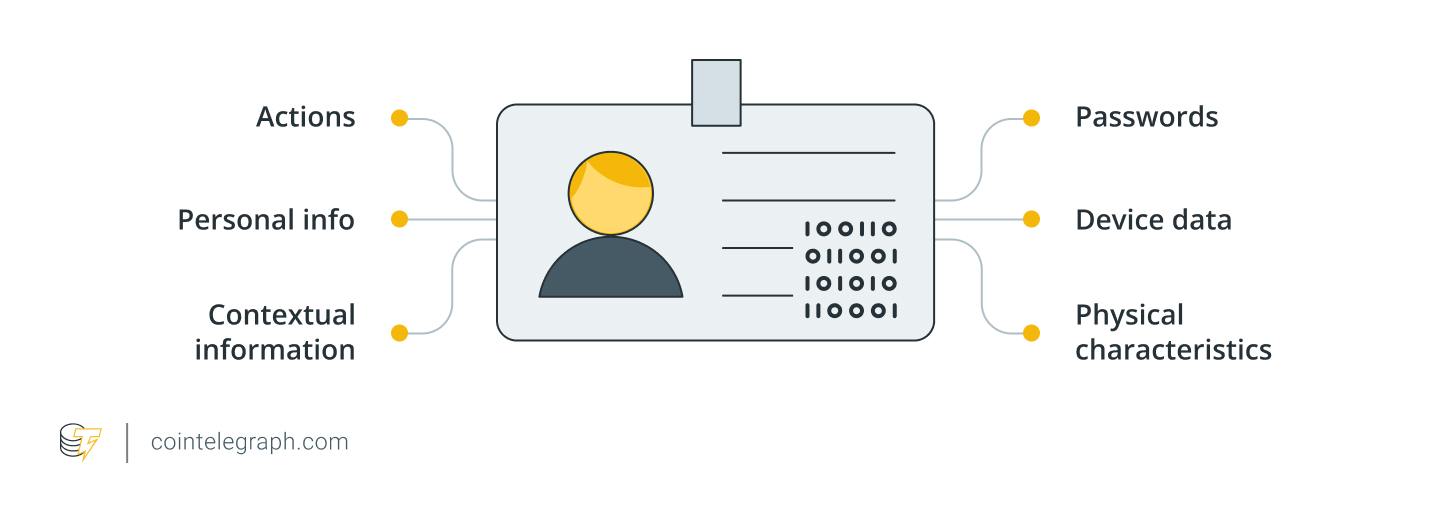
Without strong protection, even small pieces of stolen information can be stitched into a full profile, giving cybercriminals everything they need to impersonate you, seize your funds or lock you out of your accounts.
What many don’t realize is how quickly this exposure happens. Every new wallet connection, exchange login, or saved payment method quietly expands your digital surface area. With each step, your data becomes more valuable and more vulnerable. In a landscape where information is currency, your cyber identity can become a jackpot for hackers who know how to cash it out.
Did you know? In 2025, experts estimate that over 50 billion digital identities could be compromised worldwide, a 22% jump from last year. Crypto users are among the biggest targets, especially on decentralized finance (DeFi) platforms without strong identity checks. Synthetic identity fraud is also exploding, hitting new crypto lending services the hardest.
How cybercriminals steal your digital identity
Cybercriminals blend technology and manipulation to pry open digital identities.
Phishing remains a common entry point, where fake websites or emails trick users into revealing passwords or seed phrases. Large personal data breaches leak databases of usernames, emails and credentials, fueling account takeover attacks across different services.
Hackers also exploit:
- Synthetic identity fraud: combining real and fake data to create new identities.
- Social engineering attacks: manipulating users emotionally to voluntarily reveal sensitive information.
- Credential stuffing: using leaked passwords on other platforms, hoping users reused them.
Knowing how criminals exploit crypto markets and digital ecosystems can make it much harder to be tricked.
Stolen identity, sold forever on the dark web
Once your data is stolen, it often ends up for sale on the dark web, multiplying the threat.
Dark web identity theft is a thriving economy. Full identity profiles, including names, emails, Social Security Numbers (SSNs) and crypto keys can fetch high prices. Buyers may use the stolen identity immediately or resell it repeatedly, creating multiple waves of attacks months or even years later.
Even after you lock down your accounts, your leaked data can keep circulating in dark corners of the web. That’s why tools like dark web monitoring and breach alerts aren’t optional; they’re your long-term defense. Recovery isn’t a one-time fix. It’s a habit of staying alert and adapting.
Signs your digital identity has been stolen
Spotting the signs of identity theft early can stop criminals before they cause major damage.
Victims of cyber identity theft may notice strange transactions, denied logins or devices appearing that they don’t recognize. Sometimes the signs are financial — unauthorized credit card charges, changes in your crypto balances or unexpected loans under your name.
Key warning signs include:
- Password reset requests you didn’t initiate.
- Locked-out accounts or sudden logouts across devices.
- New accounts or credit lines appearing on your financial history.
- Unexpected withdrawals or transfers from crypto wallets.
By catching the signs of identity theft early, you can shut down fraud before it spirals, and protect your money and your name.
What to do if your identity is stolen
Fast, clear action gives you the best chance to limit the damage from identity theft.
If you realize your identity has been stolen, the first priority is locking down access. Update your passwords across all platforms, enable two-factor authentication (2FA) protection, and revoke access to any suspicious sessions or devices. Most major exchanges, banks and crypto services allow you to temporarily freeze your accounts while you investigate.
Beyond immediate security steps, you should report the incident to authorities and file a case with your local cybercrime unit or financial protection agency.
Using online help services can speed up your response plan. These initial moves through clear recovery steps are critical to regaining control before criminals spread the attack further.
Recovery steps after digital identity theft
Recovering from identity theft involves more than just securing your passwords; it’s a complete rebuild of your digital trust.
After locking down your accounts and alerting key institutions, you need to start active monitoring. This means regularly reviewing your bank statements, checking your crypto wallets for unauthorized transactions and inspecting your credit report for any new activity.
Some victims also pursue:
- Filing fraud alerts or credit freezes with major credit agencies.
- Hiring professional identity recovery services.
- Exploring identity theft insurance to cover legal and investigative costs.
Full recovery can take months, but a systematic approach reduces financial and emotional damage.
How to protect your digital identity
Good security habits are the strongest defense against cybercriminals.
Crypto platforms and companies should adopt decentralized blockchain-based identity solutions. These systems ensure that your data remains secure, transparent and in your control, making it much harder for hackers to manipulate or steal your personal information.
Unlike centralized systems, blockchain-based identities are stored on a distributed ledger, reducing single points of failure and making it significantly more difficult for cybercriminals to gain unauthorized access. Furthermore, decentralized identity systems enable users to verify their identities without exposing sensitive personal data, allowing for more privacy and control over who sees their information.
For users, fortifying their digital identity isn’t about ticking boxes; it’s about building sharp habits that evolve with the risks. Here’s how to stay ahead:
- Treat passwords like armor: Use strong, unique combinations for every account. A password manager can forge and guard them better than memory ever could.
- Double down with 2FA: One password isn’t enough, so add an extra lock on every door worth protecting, especially your finances and crypto.
- Practice digital minimalism: Every birthday, pet name or photo shared online can become ammo for hackers.
- Choose smart allies: Stick with crypto platforms that prioritize decentralized digital identity verification and real security, not just flashy promises.
- Watch, detect, respond: Set alerts and monitor your accounts. Spotting strange activity early can turn a disaster into a close call.
- Be stingy with your data: Only trust platforms that collect the bare minimum. If a site asks for too much, walk away.
- Avoid easy mistakes: Public WiFi is a hacker’s playground. Use a VPN when you connect, and regularly check if your credentials have leaked.
The less you reveal, the safer you stay.
Update, review, repeat: Your digital identity depends on it
Maintaining your digital identity is a daily practice, not a one-time setup.
Regularly update your passwords and security settings. Review app permissions, device authorizations and wallet connections at least every few months. Incorporating biometric authentication (fingerprints or facial scans) adds a critical physical layer of protection beyond passwords.
Understanding how hackers manipulate crypto — from phishing for private keys to setting traps with fake decentralized applications (DApps) — is what keeps you a step ahead. In today’s world, staying sharp about cybersecurity isn’t optional. It’s a basic survival skill, right up there with managing your money or protecting your home.
The future will only become more digital and more decentralized. Defending your digital identity today means preserving your independence tomorrow.
What is digital identity? Your digital identity is the fingerprint you leave across the internet, a living map of who you are.Your digital identity is more than just your name or email; it stretches from your social media profiles and crypto wallet addresses to your device fingerprints and even the rhythms of your daily browsing habits. In the fast-moving world of cryptocurrency, where identity and financial access often overlap, digital identity theft isn’t just a nuisance; it’s an open door to your assets. Without strong protection, even small pieces of stolen information can be stitched into a full profile, giving cybercriminals everything they need to impersonate you, seize your funds or lock you out of your accounts.What many don’t realize is how quickly this exposure happens. Every new wallet connection, exchange login, or saved payment method quietly expands your digital surface area. With each step, your data becomes more valuable and more vulnerable. In a landscape where information is currency, your cyber identity can become a jackpot for hackers who know how to cash it out.Did you know? In 2025, experts estimate that over 50 billion digital identities could be compromised worldwide, a 22% jump from last year. Crypto users are among the biggest targets, especially on decentralized finance (DeFi) platforms without strong identity checks. Synthetic identity fraud is also exploding, hitting new crypto lending services the hardest. How cybercriminals steal your digital identity Cybercriminals blend technology and manipulation to pry open digital identities.Phishing remains a common entry point, where fake websites or emails trick users into revealing passwords or seed phrases. Large personal data breaches leak databases of usernames, emails and credentials, fueling account takeover attacks across different services.Hackers also exploit:Synthetic identity fraud: combining real and fake data to create new identities.Social engineering attacks: manipulating users emotionally to voluntarily reveal sensitive information.Credential stuffing: using leaked passwords on other platforms, hoping users reused them.Knowing how criminals exploit crypto markets and digital ecosystems can make it much harder to be tricked. Stolen identity, sold forever on the dark web Once your data is stolen, it often ends up for sale on the dark web, multiplying the threat.Dark web identity theft is a thriving economy. Full identity profiles, including names, emails, Social Security Numbers (SSNs) and crypto keys can fetch high prices. Buyers may use the stolen identity immediately or resell it repeatedly, creating multiple waves of attacks months or even years later.Even after you lock down your accounts, your leaked data can keep circulating in dark corners of the web. That’s why tools like dark web monitoring and breach alerts aren’t optional; they’re your long-term defense. Recovery isn’t a one-time fix. It’s a habit of staying alert and adapting. Signs your digital identity has been stolen Spotting the signs of identity theft early can stop criminals before they cause major damage.Victims of cyber identity theft may notice strange transactions, denied logins or devices appearing that they don’t recognize. Sometimes the signs are financial — unauthorized credit card charges, changes in your crypto balances or unexpected loans under your name.Key warning signs include:Password reset requests you didn’t initiate.Locked-out accounts or sudden logouts across devices.New accounts or credit lines appearing on your financial history.Unexpected withdrawals or transfers from crypto wallets.By catching the signs of identity theft early, you can shut down fraud before it spirals, and protect your money and your name. What to do if your identity is stolen Fast, clear action gives you the best chance to limit the damage from identity theft.If you realize your identity has been stolen, the first priority is locking down access. Update your passwords across all platforms, enable two-factor authentication (2FA) protection, and revoke access to any suspicious sessions or devices. Most major exchanges, banks and crypto services allow you to temporarily freeze your accounts while you investigate.Beyond immediate security steps, you should report the incident to authorities and file a case with your local cybercrime unit or financial protection agency. Using online help services can speed up your response plan. These initial moves through clear recovery steps are critical to regaining control before criminals spread the attack further.Recovery steps after digital identity theftRecovering from identity theft involves more than just securing your passwords; it’s a complete rebuild of your digital trust.After locking down your accounts and alerting key institutions, you need to start active monitoring. This means regularly reviewing your bank statements, checking your crypto wallets for unauthorized transactions and inspecting your credit report for any new activity.Some victims also pursue:Filing fraud alerts or credit freezes with major credit agencies.Hiring professional identity recovery services.Exploring identity theft insurance to cover legal and investigative costs.Full recovery can take months, but a systematic approach reduces financial and emotional damage. How to protect your digital identity Good security habits are the strongest defense against cybercriminals.Crypto platforms and companies should adopt decentralized blockchain-based identity solutions. These systems ensure that your data remains secure, transparent and in your control, making it much harder for hackers to manipulate or steal your personal information.Unlike centralized systems, blockchain-based identities are stored on a distributed ledger, reducing single points of failure and making it significantly more difficult for cybercriminals to gain unauthorized access. Furthermore, decentralized identity systems enable users to verify their identities without exposing sensitive personal data, allowing for more privacy and control over who sees their information.For users, fortifying their digital identity isn’t about ticking boxes; it’s about building sharp habits that evolve with the risks. Here’s how to stay ahead:Treat passwords like armor: Use strong, unique combinations for every account. A password manager can forge and guard them better than memory ever could.Double down with 2FA: One password isn’t enough, so add an extra lock on every door worth protecting, especially your finances and crypto.Practice digital minimalism: Every birthday, pet name or photo shared online can become ammo for hackers. Choose smart allies: Stick with crypto platforms that prioritize decentralized digital identity verification and real security, not just flashy promises.Watch, detect, respond: Set alerts and monitor your accounts. Spotting strange activity early can turn a disaster into a close call.Be stingy with your data: Only trust platforms that collect the bare minimum. If a site asks for too much, walk away.Avoid easy mistakes: Public WiFi is a hacker’s playground. Use a VPN when you connect, and regularly check if your credentials have leaked.The less you reveal, the safer you stay. Update, review, repeat: Your digital identity depends on it Maintaining your digital identity is a daily practice, not a one-time setup.Regularly update your passwords and security settings. Review app permissions, device authorizations and wallet connections at least every few months. Incorporating biometric authentication (fingerprints or facial scans) adds a critical physical layer of protection beyond passwords.Understanding how hackers manipulate crypto — from phishing for private keys to setting traps with fake decentralized applications (DApps) — is what keeps you a step ahead. In today’s world, staying sharp about cybersecurity isn’t optional. It’s a basic survival skill, right up there with managing your money or protecting your home.The future will only become more digital and more decentralized. Defending your digital identity today means preserving your independence tomorrow. digital identity Cointelegraph.com News


















































































































